16 Mar Wintriage: The Triage tool for Windows DFIRers
Throughout my life, my daily job has been purely related to cybersecurity. But the branch I like the most is Incident Response and Forensics. So, I work as DFIRer.
For many years, I have used IRTriage and Windows Live Response for the triage phase in Windows’ victim systems. With them, I acquired Windows artifacts on dozens of incidents for further analysis in laboratory machines.
Those tools are great, but the extracted info is not always enough. Both complement themselves but are not able to extract everything I need in most of the cases. There are situations you know which artifacts subset you need. IRTriage and Windows Live Response are not as granular as would it be desired, they only select what is needed in those scenarios.
So, in 2019 I decided to start writing my own tool. I designed it to be able to extract the most artifacts as possible, but it also allows the user to select which artifacts get. I also considered the performance, the ability to be executed via GUI and CLI, to protect the victim system without installing software,compatible with 32 and 64bits architectures, supporting since 2003/XP in advance, and consuming as less memory as possible, of course.
What is Wintriage able to?
Wintriage is a live response tool that extracts Windows artifacts. It must be executed with local or domain administrator privileges and recommended to be done from an external drive.
It is not able to do everything by its own, so it needs to call other tools to do the job.
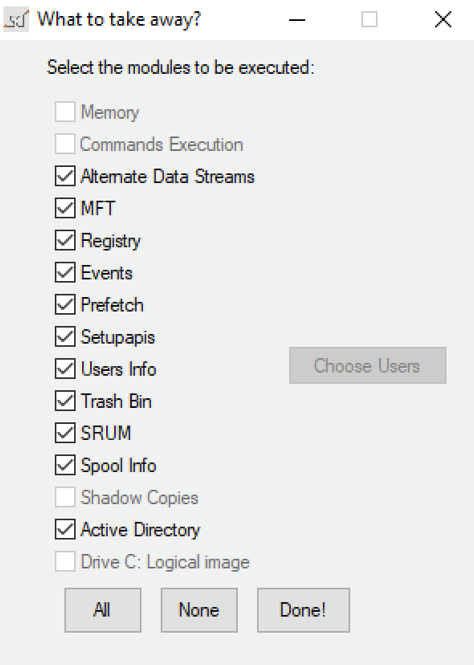
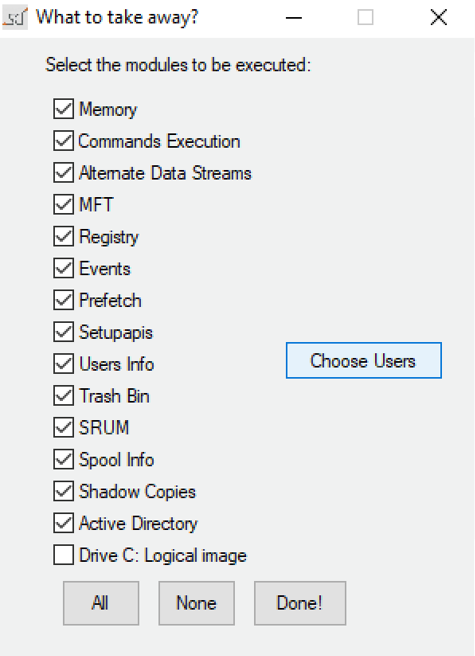 So far, it gets the next artifacts, if selected (following forensics best practices based in volatility order):
So far, it gets the next artifacts, if selected (following forensics best practices based in volatility order):
- Memory dump
- Prefetch
- Commands execution (some of them are native operating system ones and other external tools calls) to get a bunch of live information, network capture, etc…
- Info about encrypted volumes: bitlocker recovery key, truecrypt and veracrypt warnings if mounted
- Alternate Data Streams in every mounted volume
- Windows Registry
- Events: EVT/EVTX and ETL
- SRUM
- Failed spool Jobs
- All users Trash bin in every logical volume
- Active Directory ntds.dit (if executed in a Domain Controller)
- Users artifacts: Registry, shellbags, browsers (IE, Edge, Edge Chromium, Chrome, Firefox, Brave and Opera), Jumplist, Recent, Office Recent, etc…
- Shadow copies. The same artifacts in every shadow copy the system has.
- Live forensic image. It does a live image of C:\ Logical drive in EWF format. This is useful in case the volume is encrypted, so the physical image could be more complicated to be processed later.
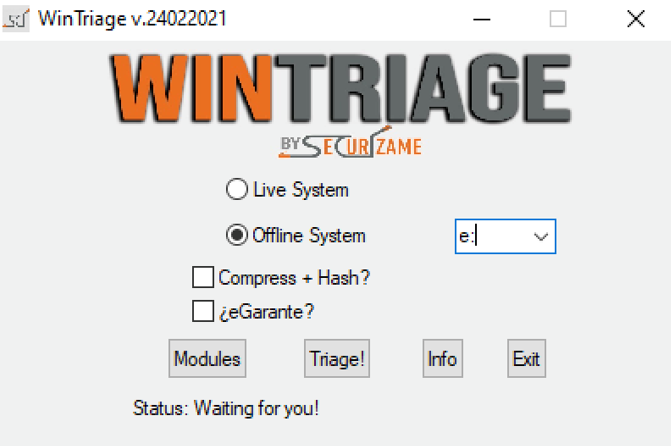
Dead systems triage
Although Wintriage is a triage tool for live Windows systems, I wanted to get artifacts from Windows forensic images. So I implemented a way to do it, but previously the C:\ logical drive from Windows forensic image needs to be mounted in a different letter of the analysis machine, making use of FTK Imager Lite, for example.
Then it will be able to extract the same artifacts as live systems, except for Memory Dump, Command execution, shadow copies and Live forensics image.
Compress and Hash
Sometimes it is interesting (or even mandatory) to take out only one compressed file and obtain its hash SHA-256. Wintriage implements this as an option.
eGarante
Only if you have an account in this service (https://www.egarante.com), Wintriage can send the SHA-256 of the compressed file to eGarante and you will receive an email with a signed PDF containing the received SHA-256. This procedure will certify the existence of that hash at that date and time.
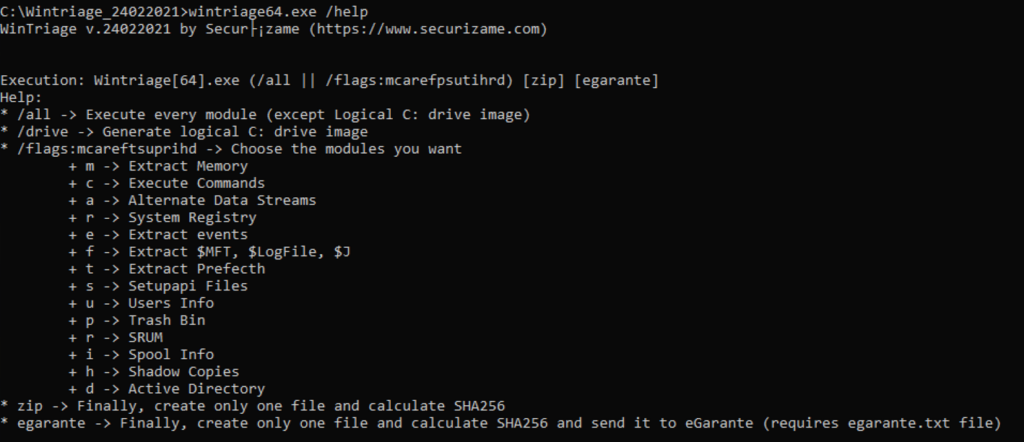
CLI
If you don’t like GUI tools or you need to triage a Windows Server Core, you can execute Wintriage via CLI in a terminal executed with elevated privileges.
ChangeLog
- In March 2020, I released the first version. I am from Spain, so the GUI and documentation were only in Spanish at that time. Several forensic investigator guys from Spanish and LATAM communities tested and reported some bugs and new suggestions to be integrated into the roadmap.
- In September 2020, a new version with some minor changes was released.
- In March 2021, the last version was released. I focused on implementing in the tool everything I had in the roadmap (network capture, last browsers artifacts, more granularity selecting users and several fixes and minor features). The most important thing in this version was the multi-language support: Spanish and English. If the victim system has been installed from a Spanish language ISO, the tool will show everything in Spanish. Otherwise, it will do it in English.
Roadmap
Currently, there are no more functionalities to be implemented, and other known bugs to fix. Of course, I will keep it updated, if more artifacts are needed to be extracted for our investigations. We use it for DFIR triage on Windows live systems so I am the first interested person that wants it is not become obsolete.
I want Wintriage!
How much does it cost?
Nothing! Wintriage is completely FREE to be used for your Windows investigations. If the COVID pandemic situation ever ends, I will thank with a coffee or a beer if it was useful for you, or even just a “Thanks for the tool! It worked OK”.
Before downloading
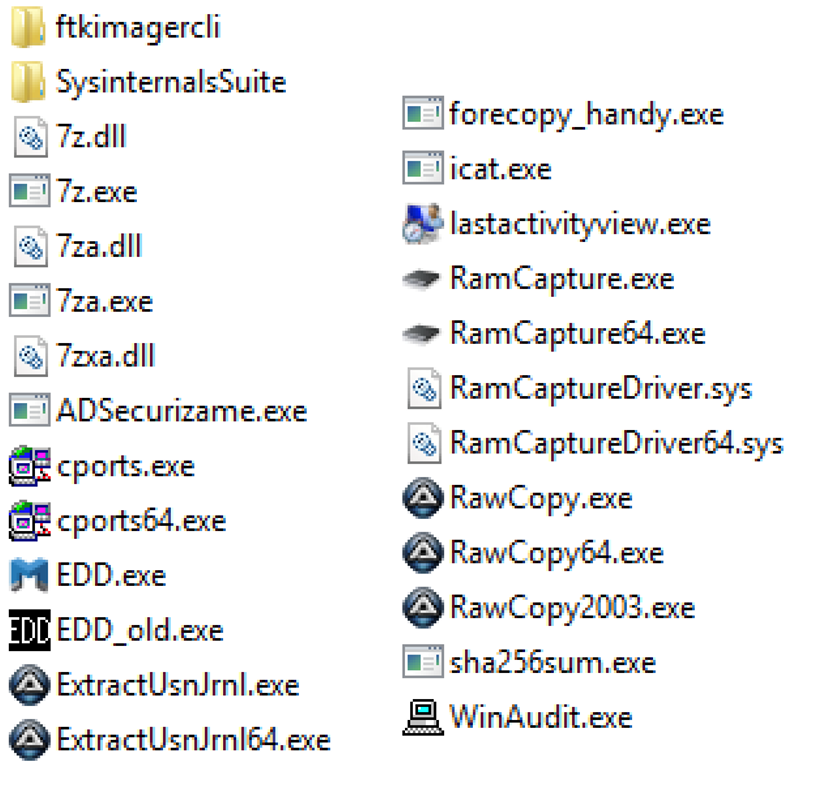
Wintriage distributable binaries are only three executables: Wintriage.exe, Wintriage64.exe and ADSecurizame.exe (in the Tools directory).
But more free tools, which their licenses don’t allow to be distributed directly, need to be downloaded and set under the Tools directory.
Here you have the sources where to download them:
– https://accessdata.com/product-download/windows-32bit-3-1-1 -> Leave the directory ftkimagercli uncompressed
– https://download.sysinternals.com/files/SysinternalsSuite.zip -> Uncompress under the SysinternalsSuite directory
– https://belkasoft.com/ram-capturer -> Ramcapture(64).exe + RamCaptureDriver(64).sys
– https://github.com/jschicht/ExtractUsnJrnl/commit/master -> ExtractUsnJrnl.exe and ExtractUsnJrnl64.exe (Important!!! Version 1.0.0.2*)
– https://www.7-zip.org/download.html (Download instalable version and once installed get 7z.dll, 7z.exe, 7za.dll, 7za.exe and 7zxa.dll files from instalation path)
– https://nirsoft.net -> cports.exe, cports64.exe and lastactivityview.exe
– http://www.parmavex.co.uk/winaudit.html -> Winaudit.exe
– https://www.magnetforensics.com/resources/encrypted-disk-detector/ -> EDD.exe (Current version is 3.0.1. If you get version 2.X of this tool, please download it in the directory Tools and rename it with edd_old.exe, besides the new one)
– https://github.com/jschicht/RawCopy/commit/master -> Rawcopy.exe and rawcopy64.exe (Important!!! Version 1.0.0.9*)
–https://github.com/jschicht/RawCopy/releases/download/1.0.0.19/RawCopy_v1.0.0.19_.Win2000.zip -> Uncompress and rename to RawCopy2003.exe
– https://github.com/proneer/Tools/tree/master/forecopy -> forecopy_handy.exe
– https://github.com/AJMartel/IRTriage/blob/master/Compile/Tools/sleuthkit-4.2.0/bin/icat.exe -> icat.exe (Important!! Download this version from this source, as it does not depend on other libraries, having everything it needs included in this single exe)
– https://kanguru.zendesk.com/hc/en-us/articles/235228027-SHA256-Checksum-Utilities -> sha256sum.exe
Download
Wintriage binaries (remember to download the other tools you need) can be downloaded from https://cursos.securizame.com/extra/Wintriage.7z
Current version SHA-256 is b3b2c36b8e2e75049ccc9fae9eec69f18e9714e49c4e969c972e5fff236b9fe6
As it has been developed with AutoIt, both executables, and even several of its dependencies, are detected as malware by several AVs. You will have to disable the AV or create an exception in the local AV when you download it and also in the victim system when you connect the drive with Wintriage.
Enjoy Wintriage!
Contact me
If you need me, contact me at @Lawwait or send me an email to contacto@securizame.com.
Lorenzo Martínez Rodríguez
CTO at Securízame